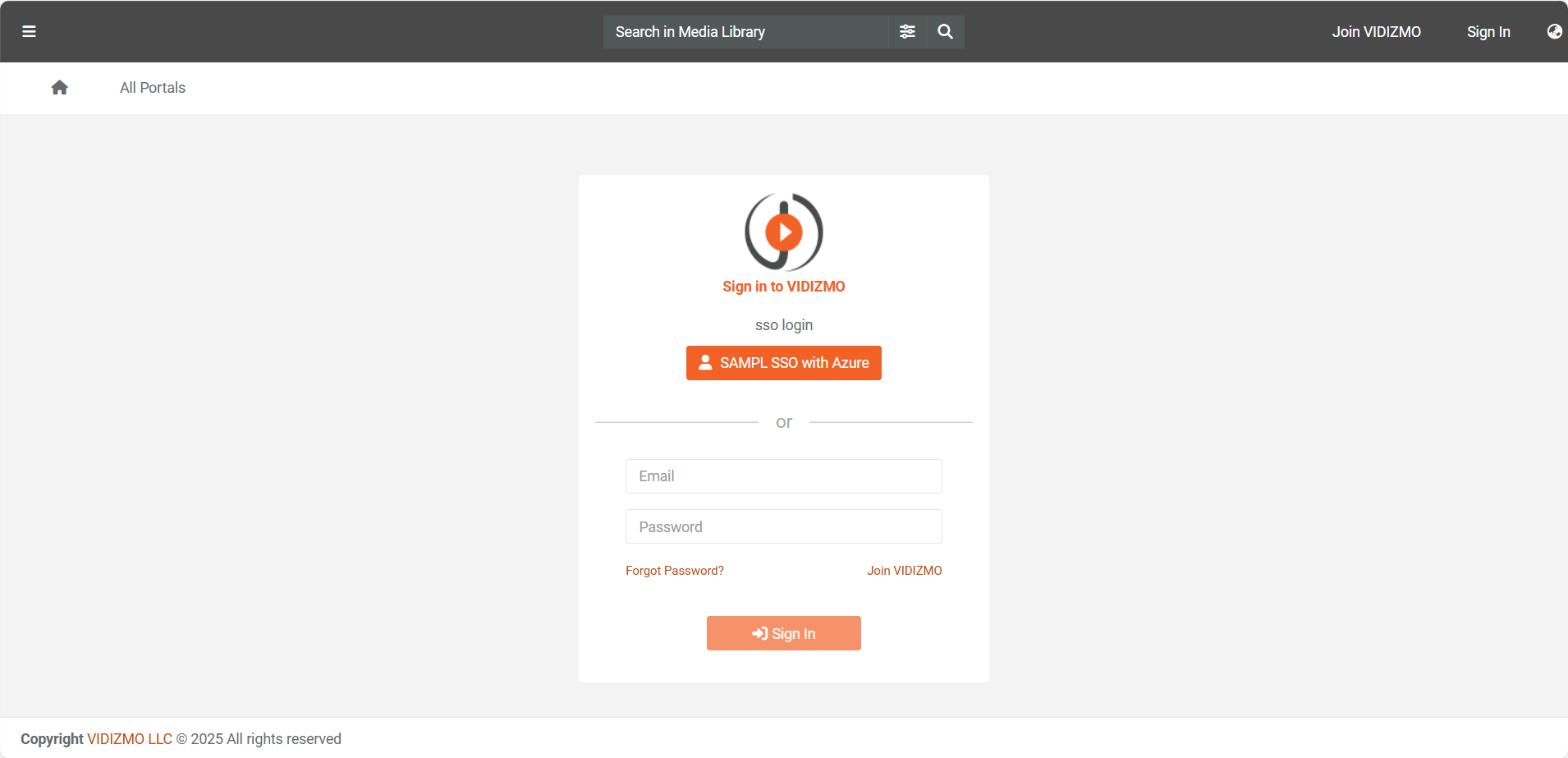
How to Setup SAML-P SSO using Azure
In VIDIZMO, you can use the SAML protocol for Single Sign-On (SSO) with Microsoft Entra ID (formerly Azure Active Directory). This allows users to authenticate once and access application without needing to re-enter credentials. This article explains how to configure and use SSO with SAML in VIDIZMO. For further information, refer to the VIDIZMO SSO Apps documentation.
Before you start
- Ensure that you belong to a group where the Management of SSO + SCIM permission is enabled to access this feature to configure SAML-P SSO using Microsoft Entra ID.
- For configuring Microsoft Entra ID SSO with SAML, you must have an Microsoft Entra ID account so that you can create an new application. For creating an account, visit.
- If more SSO Apps have been configured and enabled on your Portal other than your users will see multiple buttons on the login page allowing them to choose any identity provider of their choice to log in to their VIDIZMO Portal.
Configuration in Azure Portal
Creating Application
To create an application in your Azure portal that uses the Security Assertion Markup Language (SAML) protocol for authentication and single sign-on, you can utilize the Enterprise Applications feature. This allows you to create and register a SAML-based application where you can view and manage its properties.
- Sign in to the Microsoft Entra admin center
- Navigate to Entra ID > Enterprise apps.
- Select Create your own application.
- In the Create your own application pane, provide a name for your application.
- Select third option "Integrate any other application you don't find in the gallery (Non-gallery)"
- Select Create to finalize the process.

Set up SSO with SAML
- In the enterprise application you just created, click the Manage tab.
- Under the Manage tab, select the Single Sign-On option.
- Choose SAML as the single sign-on method.
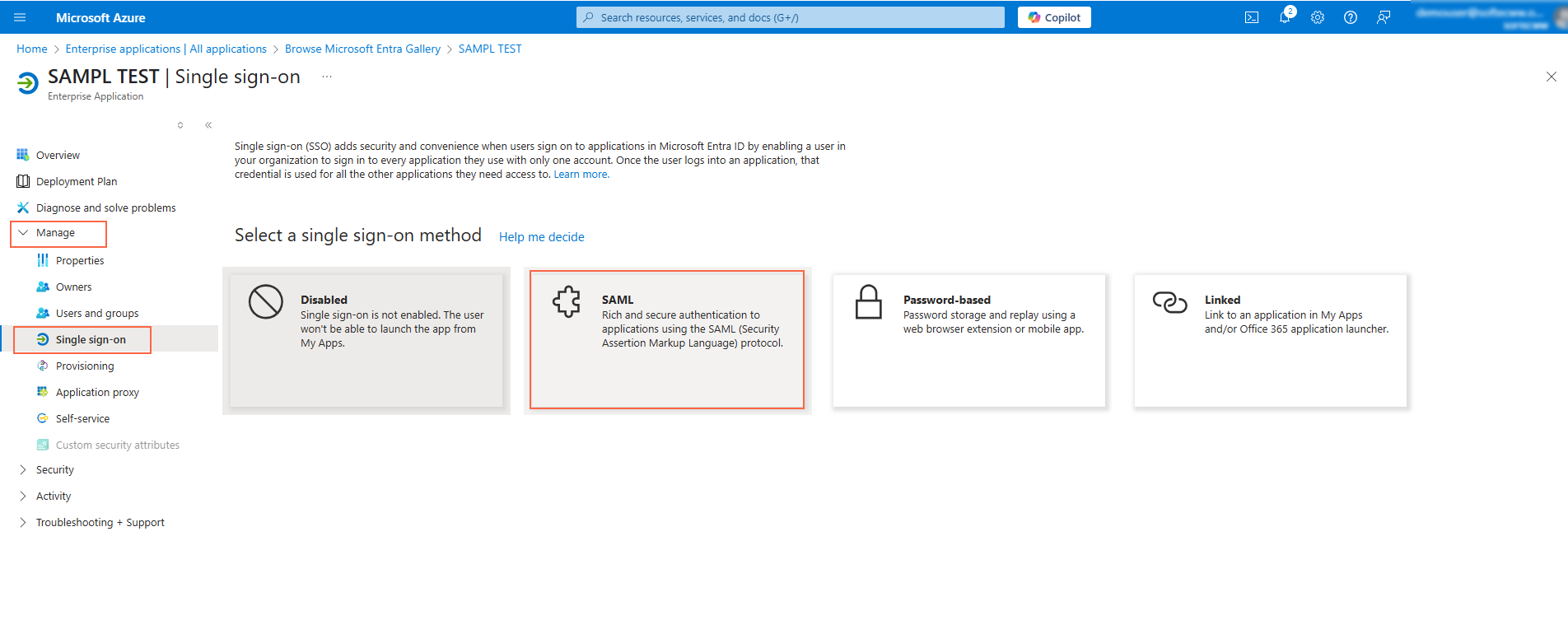
- Click Edit in the Basic SAML Configuration section to open the configuration pane.
- Enter the Identifier (Entity ID), which should be your VIDIZMO portal URL (e.g.,
https://<vidizmo portal>.com/). - Add the Reply URL (Assertion Consumer Service URL), for example:
https://<vidizmo portal>.com/Saml2/Acs. - Click Save to apply the changes.
Attribute and Claims (Optional)
- Click Edit in the Attributes&Claims section.
- Click "Add new claim" option.
- On Manage claim page, enter the name of the claim in Name field.
- In the Namespace field, enter only the base namespace URI
(e.g., http://schemas.xmlsoap.org/ws/2005/05/identity/claims). Do not include the specific VIDIZMO attribute suffix such as /givenname when pasting this value. - Select Attribute as the source.
- Enter the source attribute name.
- Click Save.

Retrieving EntityID via App Federation Metadata Url
- In the SAML Certificates section, locate the App Federation Metadata Url.
- Copy the entire Url value.
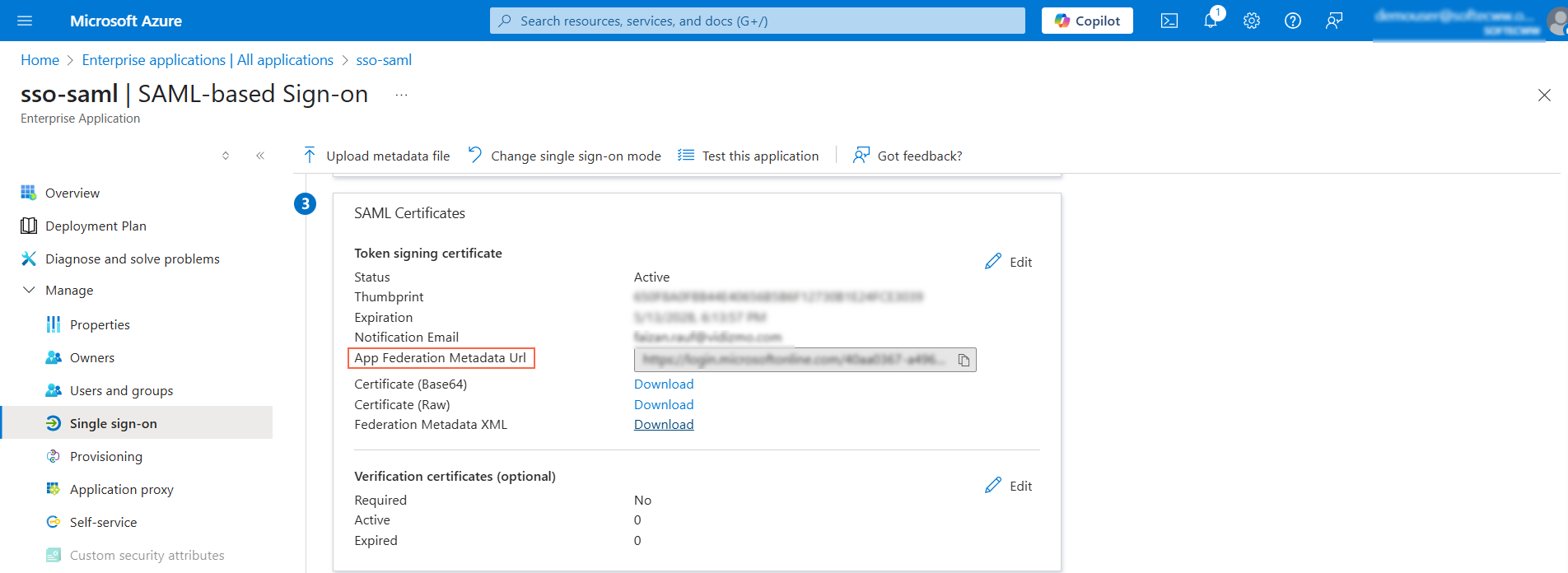
- Open a web browser and paste the copied Url into the address bar, then press Enter.
- An XML metadata file will open in the browser.
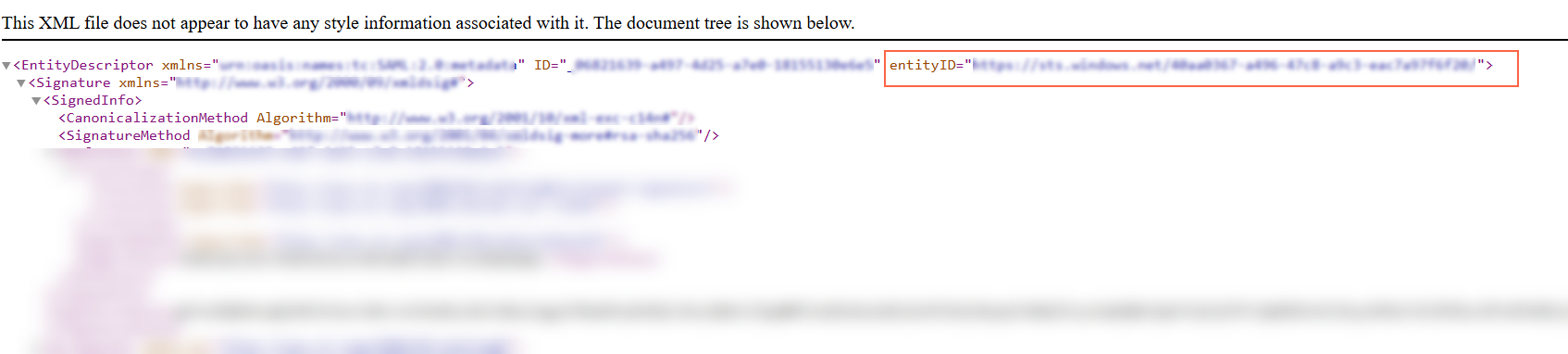
- Search the XML file for the entityID attribute.
- Copy the value of the entityID attribute.
- Save the copied entityID value securely,you will need it later when configuring the SAML application in the VIDIZMO portal.
Configuration in VIDIZMO Portal
- From the Portal's Homepage click on the navigation menu.
- Expand the Admin tab.
- Click on the Portal Settings tab.
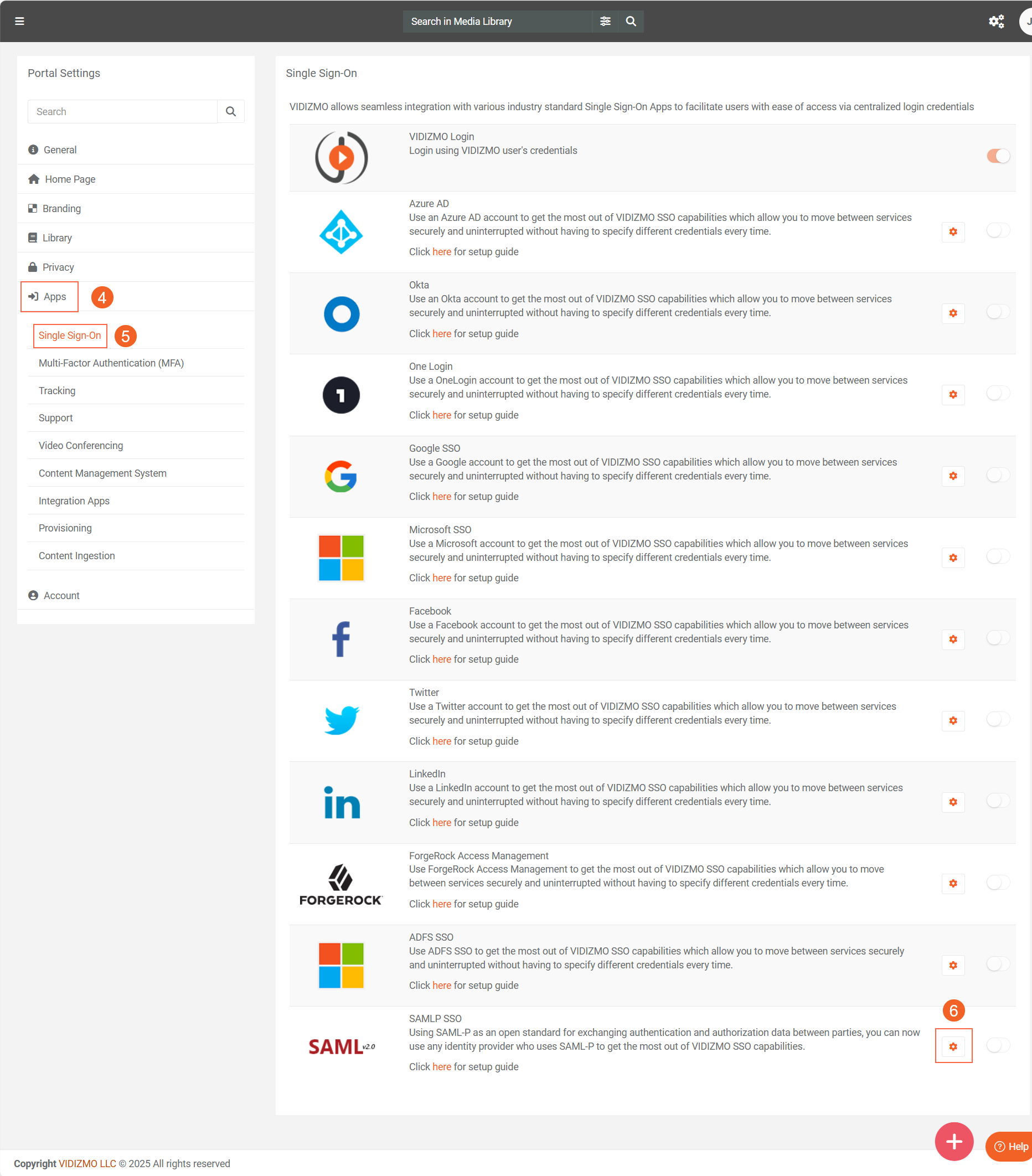
- From Portal Settings page, click on the Apps tab.
- Further click on the Single Sign-On tab.
- Locate the SAML at the right-hand side and click on the gear icon to open SAML P SSO - Settings.
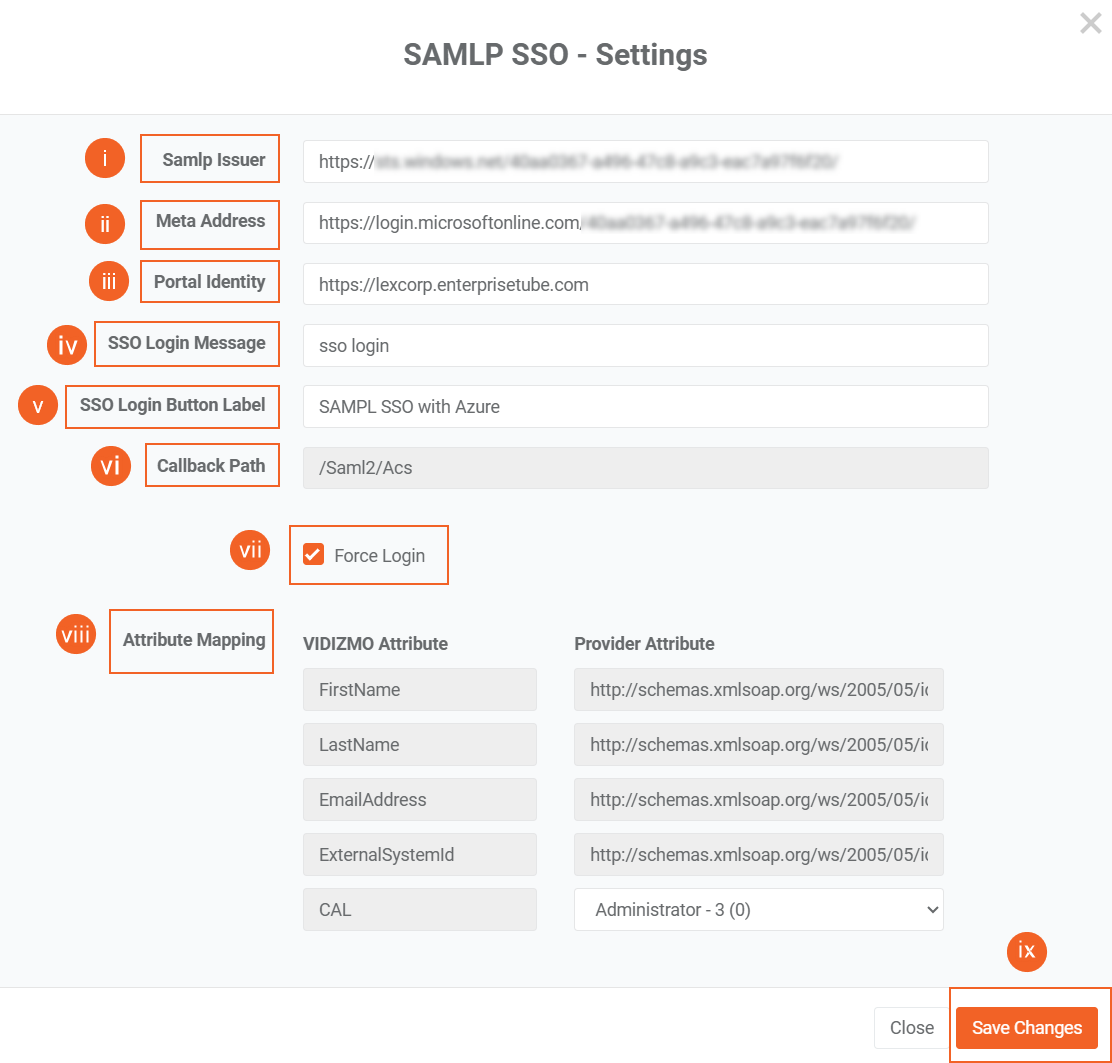
- In the SAML P SSO - Settings screen:
i. Samlp Issuer: Enter the entityID saved earlier.
ii. Meta Address:: Enter here App Federation Metadata Url.
iii. Portal Identity: Your portal URL e.g.
https://lexcorp.enterprisetube.comiv. SSO Login Message: Enter here the message that you want to display on your portal login screen for Azure login. v. SSO Login Button Label: The text entered here would display on the button used for Azure login. vi. Callback Path: Specifies the callback location where the authorization will be sent to your Portal. vii. Force Login: Select the checkbox to enable forced login. VIDIZMO uses your existing Azure session (if you're already signed in to Azure) and lets you into the portal without prompting for credentials. viii. Attribute Mapping: Attribute Mapping allows you to map your attributes with the IDP's attributes.
- If multiple CAL (Client Access License) types are available in your VIDIZMO portal, you can select the desired CAL type. This selection will be automatically applied to all users who log in to the VIDIZMO portal using Azure SSO.
- Note that after the automatic sign-in and CAL assignment, the number of available CALs should be dynamically decreased and reflected consistently across all application screens displaying the remaining count, such as on the consumption screens.
ix. Click on the button Save Changes.
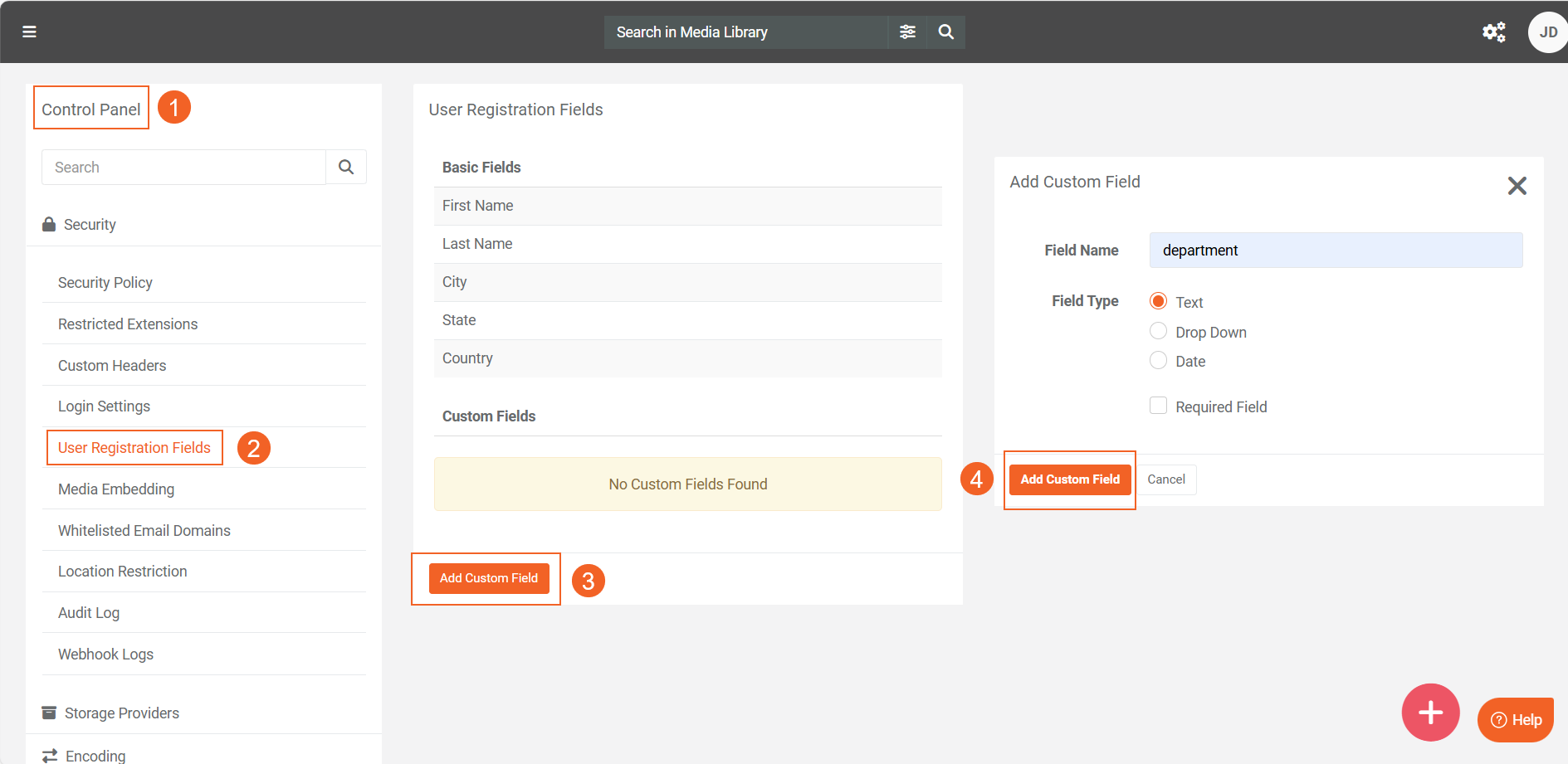
Adding Custom Attribute Mapping (Optional) You can add custom attributes in VIDIZMO by creating and mapping custom fields.
First create a Custom Field in VIDIZMO.
- Navigate to the Control Panel in your VIDIZMO portal.
- Go to User Registration Fields.
- Click on Add Custom Field.
- On the Add Custom Field page:
- Enter a Field Name (case-sensitive).Example:
department - Select Field Type as "Text".
- Click Add Custom Field to save the new field.
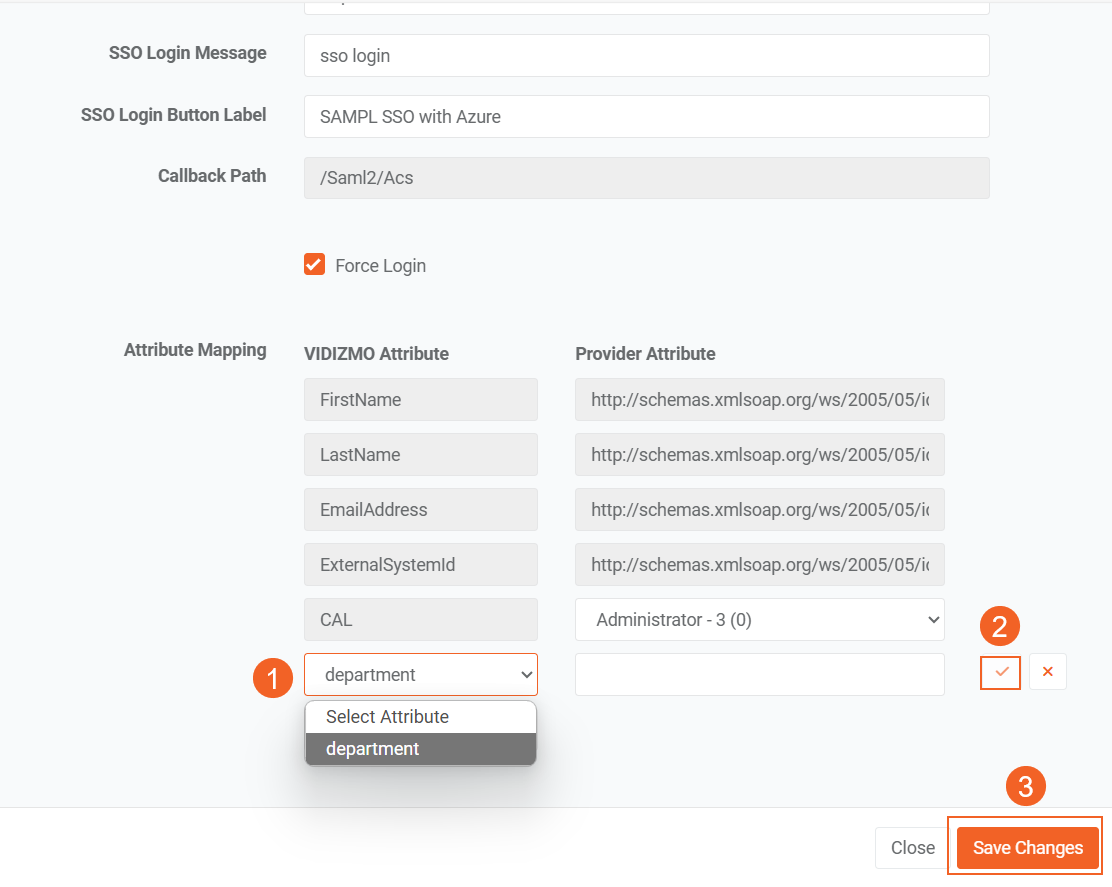
Now Map the Custom Attribute in Your SAMPL App
- In the VIDIZMO Attribute column.Click on Add New Attribute.
- Select the custom field you just created (e.g., department) from the dropdown list.
- In the Provider Attribute column,enter the corresponding SAML claim URI.
Use the following format:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/<your_custom_attribute>
- Click the checkmark icon to confirm and add the attribute.
- Click Save Changes to apply the configuration.
Note: The custom field will only work if the matching attribute and claim are added in Azure Entra ID.
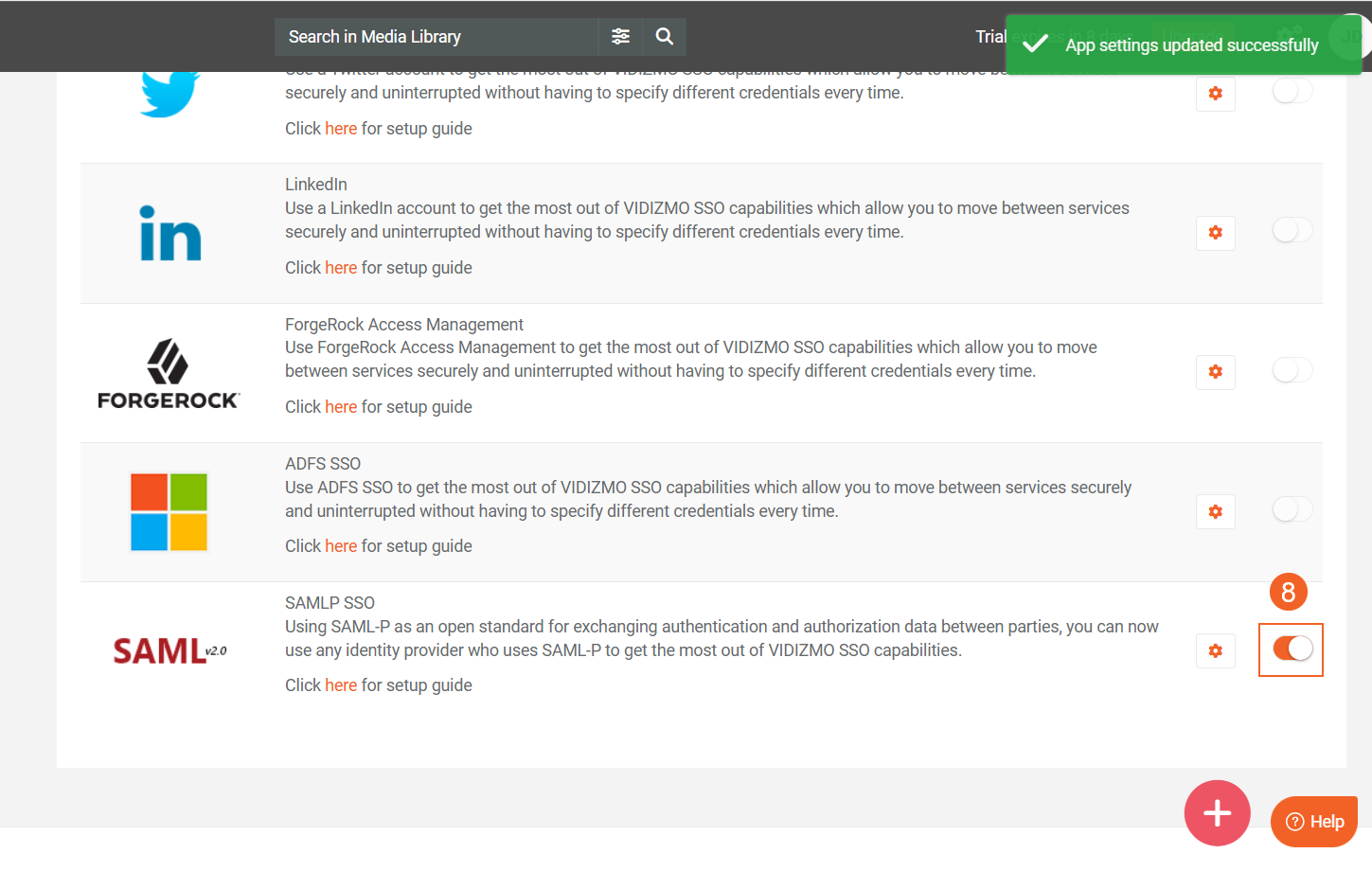
- Enable the toggle button of the SAMLP app.
Result
Navigate to the Portal's login screen and you will see an option Login with SAMLP SSO.